Millions of Google Android Android users in India face a significant risk due to a critical zero-click remote code execution vulnerability (CVE-2025-48593) in Android versions 13 to 16. This flaw allows attackers to exploit devices remotely without requiring any interaction from users, putting personal data, communication, and system integrity at serious risk.
The Indian Computer Emergency Response Team (CERT-In) has issued a high alert urging users to install the November 2025 security update released by Google and device manufacturers immediately. Samsung, Xiaomi, and other brands have also rolled out patches to address this critical threat.
CERT-In and cybersecurity experts warn that delayed updates leave millions exposed to potential hacking, data theft, and system breaches.
Details of the Vulnerability and Official Guidance
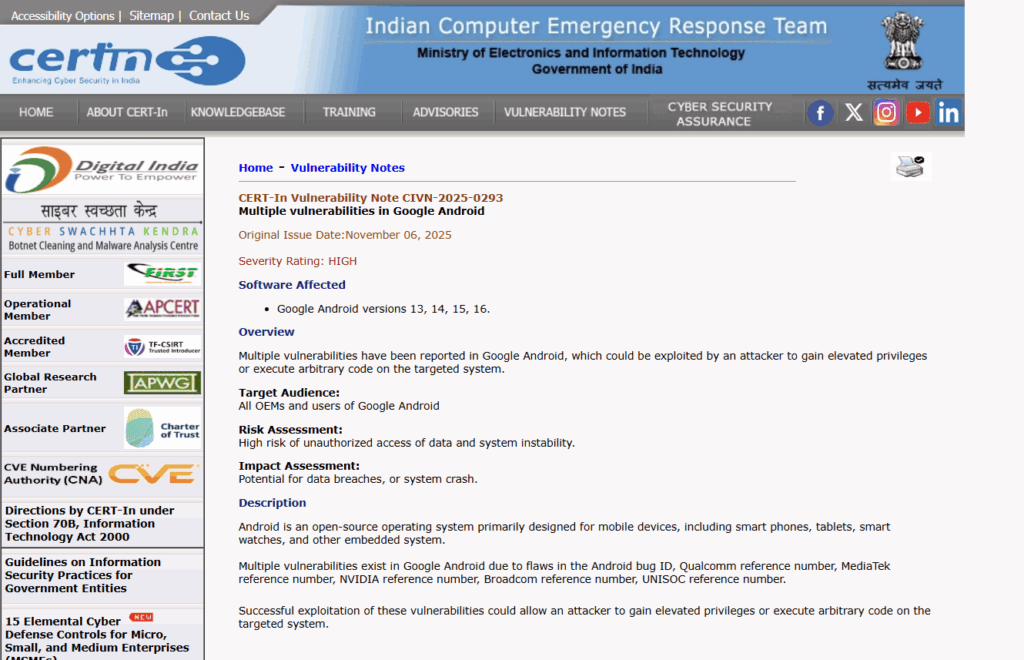
The CVE-2025-48593 vulnerability stems from insufficient validation of user input within the Android System component, enabling attackers to perform remote code execution without user interaction, a rare and highly dangerous “zero-click” exploit. Google’s November 2025 Android Security Bulletin confirms no active exploitation has been detected so far, but stresses urgency in patching devices to prevent any future attacks.
Samsung’s November security update also includes fixes for this flaw and additional high-severity vulnerabilities. Users are urged to check their device’s security patch level by navigating to Settings > About Phone > Security Patch Level and ensuring it is dated November 1, 2025, or newer. Network operators in India have begun sending out alerts encouraging users to update urgently.
Broader Cybersecurity Context in India
This alert comes amid rising mobile cyber threats targeting India, home to one of the largest Android user bases globally. Zero-click exploits like this vulnerable CVE enable silent attacks, where users remain unaware of breaches, increasing risks of data theft, ransomware, and remote surveillance.
Previous spyware campaigns like LANDFALL revealed in 2025 exploited other vulnerabilities on Android devices, highlighting a persistent wave of targeted cyberattacks. Experts emphasize that India’s low patch adoption rates exacerbate vulnerability, demanding stronger public awareness and proactive digital hygiene practices among users and organisations alike.
How to Stay Safe: Practical Steps for Users
- Update Immediately: Regularly check for and install the latest Android security patches, especially the November 2025 update that fixes CVE-2025-48593. Enable automatic updates where possible to stay protected with minimal effort.
- Check Patch Level: Go to your device’s Settings > About Phone > Security Patch Level and verify it shows 2025-11-01 or later. If not, update promptly.
- Avoid Unofficial Apps: Download apps only from official stores like Google Play, avoiding third-party sources that may host malicious software.
- Be Cautious on Networks: Use trusted Wi-Fi connections and avoid unsecured public Wi-Fi. Consider using VPNs for additional privacy.
- Use Security Features: Activate device encryption, strong screen locks, and two-factor authentication where available to add layers of defence.
- Stay Alert: Monitor device behaviour for unusual apps, battery drain, or data usage, which can signal compromise. Report suspicious activity immediately.
The Logical Indian’s Perspective
Digital security is a shared responsibility essential to trust, empathy, and coexistence in our connected lives. The CVE-2025-48593 warning reminds us that protecting ourselves online is not only about technology but about safeguarding our collective dignity and peace.
The Logical Indian urges citizens to embrace continuous vigilance, timely software updates, and community education to strengthen resilience against growing cyber threats.